

I formulated this solution with AT&T USM Anywhere as the foundational Cloud-Based SIEM, although it’s versatile enough to accommodate almost any equivalent service. The primary goal of this USE CASE is to demonstrate how contemporary IT security technology can be effectively deployed to provide comprehensive security services across both IT and OT environments simultaneously.
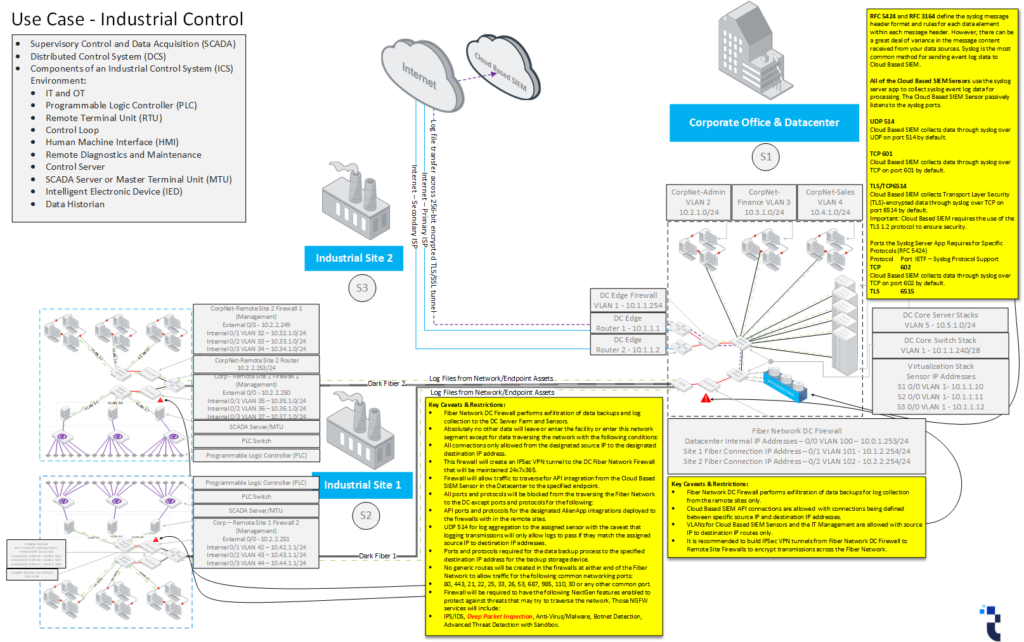
For optimal functionality, I strongly recommend the abundant use of Next-Gen or UTM Firewalls to facilitate network segmentation and enhance interconnectivity security. Prioritizing security and employing interoperable, integrated security systems are paramount to achieving the highest level of enterprise security.
My design approach stems from extensive collaboration with various OT organizations, which primarily operate critical infrastructure such as water, sewerage, electricity, and manufacturing facilities. Notably, integrating OT and SCADA environments poses unique challenges, particularly due to the inherent caution among OT managers regarding internet exposure within these environments.
Key considerations for this solution include:
For optimal functionality, I strongly recommend the abundant use of Next-Gen or UTM Firewalls to facilitate network segmentation and enhance interconnectivity security. Prioritizing security and employing interoperable, integrated security systems are paramount to achieving the highest level of enterprise security.
My design approach stems from extensive collaboration with various OT organizations, which primarily operate critical infrastructure such as water, sewerage, electricity, and manufacturing facilities. Notably, integrating OT and SCADA environments poses unique challenges, particularly due to the inherent caution among OT managers regarding internet exposure within these environments.
Key considerations for this solution include:
Security Oriented Convergence refers to the integration and unification of physical security, cybersecurity, and operational security systems and processes into a cohesive framework. The goal of this approach is to create a more resilient, comprehensive security posture that addresses both digital and physical threats effectively.
© 2025 Sovergence Consulting, LLC. | All Rights Reserved | Powered by Sovergence.